Blog
Arif Mehsud's OpenSSL Conference experience
We’ve been publishing the experiences of people who received a scholarship to the OpenSSL Conference. Today we hear from Arif Mehsud.

Attending the OpenSSL Conference 2025 was an inspiring experience. I was especially excited by the sessions on post-quantum cryptography and crypto-agility, which showed how OpenSSL is shaping the future of secure communications. Meeting experts and contributors from around the world highlighted the power of collaboration and shared knowledge in the open-source community.
More ...
Nikolas Gauder's OpenSSL Conference experience
Seven people who applied received a Foundation Scholarship to the OpenSSL Conference. We reached out to those who attended and asked about their experiences. Today we’re sharing Nikolas Gauder’s story.

Attending the OpenSSL Conference was an incredible opportunity to connect with people who are shaping the future of secure communication on the Internet. I’ve long been interested in the intersection of cryptography, network protocols, and open-source development, so when I saw the chance to attend, I immediately applied. I actually came across the scholarship while browsing the OpenSSL website for a project I was working on and it felt like the perfect opportunity to get engaged with the community behind one of the most widely used security libraries in the world.
More ...
Vote now for the Foundation Business Advisory Committee
The voting from the Foundation BAC has been extended through December 21. If you want to participate in the future of the OpenSSL Foundation, please join the communities site and vote for your representative.
The currently running elections are:
For details about how the election works, please consult the Foundation Election Guide.
PQC in NC
OpenSSL Foundation recently had the opportunity to partner with All Things Open on one of their meet-up events in Research Triangle Park, North Carolina. We were excited to have 150 attendees join us for this top-notch evening hosted by Cisco, one of the Foundation’s generous premier supporters.

The topic of the night was Open Source Post-Quantum Cryptography (PQC), featuring a talk by Foundation President Matt Caswell and a panel discussion with four local PQC experts:
More ...Extending the Foundation BAC nomination
By the original timeline we should be in the voting portion of the Foundation BAC election. Due to the Thanksgiving holiday last week in the United States, we’ve decided to extend the nomination deadline by a week.
The timeline for voting has been changed to:
- December 8–December 21 (14 days)—Voting
- December 21—Results Announcement
If you are interested in representing your community on the Foundation BAC, please nominate yourself.
Getting Started With Open Source

Matt Caswell, President of OpenSSL Foundation presents at the OpenSSL Conference 2025
Back in October we held the inagural OpenSSL Conference in Prague. During my keynote talk I shared the story of my beginnings with OpenSSL. This was a story of small steps. OpenSSL is large and complicated and can be quite overwhelming for the newcomer wanting to make their first contribution. Where do you even start?
More ...WISP scholars at the OpenSSL Conference

Pictured (left to right): Amy Parker, Chief Operations Officer, OpenSSL Foundation; Matt Caswell, President, OpenSSL Foundation; WISP scholars Katty Trevizo, Katrina Khanta, and Andrea Molnár; Tim Hudson, President, OpenSSL Corporation.
It’s estimated that women make up between 20-25% of the cybersecurity workforce globally. While the OpenSSL community welcomes everyone, everywhere, we know that the number of women involved with OpenSSL is quite small. As part of our focus on nurturing a larger and more diverse community, the OpenSSL Foundation and OpenSSL Corporation were pleased to partner with Women in Security and Privacy (WISP) to provide scholarships for three of its members to attend the inaugural OpenSSL Conference in Prague.
More ...OpenSSL Foundation at GitHub Universe 2025

The OpenSSL Foundation is pleased to share that Tomáš Mráz, our Public Support and Security Manager, represented the Foundation at GitHub Universe 2025, GitHub’s annual flagship conference dedicated to innovation, open source collaboration, and the future of software development.
Held in San Francisco, GitHub Universe 2025 brought together developers, security professionals, and open-source leaders from around the world to explore cutting-edge advancements in secure software practices, AI-assisted development and project management, and the evolving landscape of open collaboration.
More ...On the road in North Carolina

In mid-November, OpenSSL Foundation staff will be on the road in North Carolina, and we’d love to see you there!
Join us on Tuesday, November 18, 2025 at the All Things Open Meet-up where Foundation President Matt Caswell will speak on open source post-quantum cryptography.
Following Matt’s introduction to the topic, he’ll facilitate a panel discussion with local experts, including:
- Jai Arun, Head of Product Management & Strategy, Quantum Safe and Crypto-Agility Products, IBM Software
- Aydin Aysu, Associate Professor, University Faculty Scholar, Electrical & Computer Engineering Department, North Carolina State University
- Scott Fluhrer, Principal Engineer, Cisco
- Panos Kampanakis, Principal Security Engineer, AWS
This event takes place on November 18 at 6:30 - 8:30pm and will be hosted at Cisco’s Research Triangle Park (RTP) campus. Doors open at 6:00pm. Learn more about the event and register here.
More ...Introducing Igor Ustinov
 OpenSSL Foundation welcomes Igor Ustinov, Senior Software Engineer, as the newest member of our team. This new engineering role is partially funded through Cisco’s premier sponsorship.
OpenSSL Foundation welcomes Igor Ustinov, Senior Software Engineer, as the newest member of our team. This new engineering role is partially funded through Cisco’s premier sponsorship.
Igor has been involved with the OpenSSL project for nearly two decades, contributing his expertise and deep technical understanding to its ongoing evolution. Over the years, he has been actively engaged in extending the project’s cryptographic capabilities — adding support for new algorithms and designing the underlying infrastructure that makes such integrations efficient and sustainable.
More ...Contributors to the OpenSSL Library (September 2025)
September has come and gone, so it’s past time to recognize new contributors to the OpenSSL Library:
| author | date | PR |
|---|---|---|
| xiaoloudongfeng | 2025-09-02 | fix length of digestinfo_sm3_der |
| Pkeane22 | 2025-09-07 | Fixed typo |
| LuiginoC | 2025-09-10 | crypto/evp/bio_ok.c:Integer Overflow in BIO_f_reliable record parser leads to Out-of-Bounds Read |
| ritesh006 | 2025-09-11 | doc: clarify SSL_SESSION_get0_hostname notes |
| jedenastka | 2025-09-11 | Fix cipher protocol ID type in docs |
| leesugil | 2025-09-14 | FIPS 186-5 auxiliary prime length check condition updated (Fixed #28526) |
| rodeka | 2025-09-16 | crypto/ml_dsa: fix public_from_private() error path to return failure |
| jonathimer | 2025-09-18 | Add Linux Foundation Health Score badge to README |
| bleeqer | 2025-09-29 | ts_conf: fix memory leak in TS_CONF_set_policies |
Here are more details on a sample of these pull requests.
More ...
We Celebrate the Success of the Inaugural OpenSSL Conference in Prague

The OpenSSL Corporation and the OpenSSL Foundation celebrate the success of the inaugural OpenSSL Conference, held in Prague, October 7-9. This was the first time in the history of the OpenSSL Project that the full community met in person. Developers, legal experts, and users from academics, committers, distributions, individuals, large businesses, and small businesses came together to discuss project direction, share experience, and collaborate on the future of secure digital communication.
More ...OpenSSL 3.6: the Foundation perspective
On October 1, OpenSSL 3.6 was released. Since the Library operates on time-based releases, each version includes only features that have been merged when the code freeze happens. In this way, releases happen at a predictable time while allowing code improvements to be developed at the appropriate pace.
For instance, 3.5 included initial work on
EVP_SKEY
and that feature was fleshed out in 3.6 with support in the key
derivation and key exchange provider methods.
Foundation Business Advisory Committee election
Believe it or not, it’s time to start the election process for the 2026 Foundation Business Advisory Committee (FBAC). Advisory committees play a critical role in the governance of the OpenSSL Foundation. This committee focuses on the strategic direction of the OpenSSL Foundation and our mission.
Each of the six communities (Academics, Committers, Distributions, Individuals, Large Businesses and Small Businesses) will have a representative who will serve for one year. In addition to a monthly meeting, representatives also lead discussions on the Communities platform and generally promote the OpenSSL Mission.
More ...Introducing Ryan Hooper
 The OpenSSL Foundation welcomes Ryan Hooper as an Associate OpenSSL Foundation Engineer. Coming from Cisco Systems, Ryan will be working part-time with the OpenSSL Foundation as part of Cisco’s premier sponsorship.
The OpenSSL Foundation welcomes Ryan Hooper as an Associate OpenSSL Foundation Engineer. Coming from Cisco Systems, Ryan will be working part-time with the OpenSSL Foundation as part of Cisco’s premier sponsorship.
Ryan has been a dedicated Software Engineer at Cisco for over 17 years, specializing in security certifications for Cisco products. His expertise spans multiple programming languages and workflows, enabling him to adapt quickly and effectively across various product teams to help achieve critical certifications.
More ...Comcast Innovation Fund supports work on DTLSv1.3

We are pleased to share that the OpenSSL Foundation has received an open-source development grant from the Comcast Innovation Fund to support our work on the DTLSv1.3 feature.
DTLS is a secure transport protocol that is particularly important for live video streaming. The OpenSSL Library currently implements DTLS versions 1.0 and 1.2. The specification for DTLSv1.2 was published in 2012 and is now quite old. In 2022, the Internet Engineering Task Force published the specification for DTLSv1.3, which is a major update that implements numerous improvements. For example, it is only through DTLSv1.3 that live video streaming applications will have access to post-quantum cryptographic security and privacy features.
More ...A new mission and logo to highlight our distinct focus
The OpenSSL Foundation has been operating as an independent entity for a little over a year, and in that time we’ve made great strides in establishing our unique place in the OpenSSL ecosystem. Recently, we published a Foundation mission and launched a new logo, all with the goal of helping everyone better understand the Foundation’s role within the larger OpenSSL ecosystem.
You may already be familiar with the OpenSSL Mission, an overarching belief that is shared by everyone involved with the OpenSSL project, from us at the Foundation, to our friends at the OpenSSL Corporation, other OpenSSL Projects, and all of our communities. This project mission states: “We believe everyone should have access to security and privacy tools, whoever they are, wherever they are or whatever their personal beliefs are, as a fundamental human right.”
More ...OpenSSL in the Wild (2025)
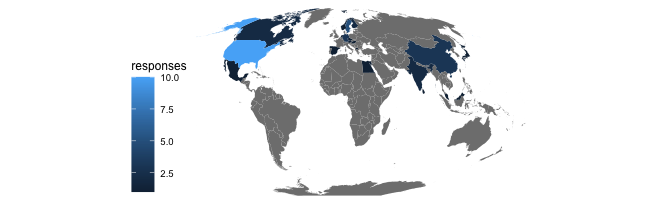
In June we asked OpenSSL users to complete a short survey. Of the 54 responses, 39 reported where they were in the world. Since this was our first survey, the sample is not as representative as we’d like. While the OpenSSL Library has a global presence, few people know that it exists or what it does. Our survey respondents are among the rare who do.
Cisco expands partnership to accelerate OpenSSL Foundation innovation and security advancements

We are honored to share that Cisco Systems has signed on as a Premier Sponsor of the OpenSSL Foundation.Their three-year sponsorship will allow the Foundation to focus on long-term projects that require multi-year funding. As a nonprofit that relies on sponsorships, donations, and grants to meet our budgetary needs, we are deeply grateful for this meaningful contribution.
Cisco’s sponsorship will help fund a new full-time software engineer at the Foundation and also add the part-time support of an engineer seconded from Cisco. Adding engineers to the team has been our top priority since the OpenSSL project’s organizational reform of last year. With these new resources, we will be able to move forward more quickly with fundamental engineering work and ongoing development of a variety of features, such as QUIC related projects, additional PQC work, and DTLS1.3.
More ...Introducing Daniel Kubec
The OpenSSL Foundation welcomes Daniel Kubec as the newest member of our team. As Senior Software Engineer, Daniel will help the Foundation continue to deliver on its mission of providing security and privacy tools to everyone, everywhere.
Daniel has worked as a contractor for over twenty years, bringing expertise in operating systems, high-throughput networks, protocols, cryptography, and security-related domains. He has a record of projects at several successful cybersecurity startups and corporations, particularly in the telecommunications sector, along with contributions to open-source security.
More ...Contributors to the OpenSSL Library (August 2025)
Among the 91 PRs approved in August, 6 were from people who hadn’t contributed to OpenSSL’s code base until now.
| author | date | PR |
|---|---|---|
| zl523856 | 2025-08-03 | [RISC-V] Further optimization for AES-128-CBC decryption performance |
| ChillerDragon | 2025-08-04 | Improve english in endian comment |
| ritoban23 | 2025-08-13 | Fix potential null pointer dereference in pkey_dh_derive |
| vkryl | 2025-08-15 | Android: Enable 16 KB ELF alignment for arm64-v8a and x86_64 platforms |
| itot1198 | 2025-08-18 | Remove unnecessary fetch-depth in GitHub Actions workflow |
| Leonabcd123 | 2025-08-28 | Fixed typo |
zl523856 started by submitting an issue that asking about the proposed change. The pull request includes some assembly code that improves the performance of the AES-128-CBC decryption algorithm on the RISC-V architecture. It’s not the sort of code that just anyone can write. Open source projects, such as OpenSSL, can benefit from one-time contributions of expertise. In turn, anyone who uses OpenSSL or products that include the library also benefit. It’s a beautiful thing.
More ...Announcing the OpenSSL Foundation Conference Scholarship recipients

The OpenSSL Foundation is pleased to announce that seven individuals have been selected to receive a Foundation Scholarship for the OpenSSL Conference in Prague on October 7-9, 2025. We are grateful for the time and attention that everyone gave to their applications, including those we were unable to fund.
The selected recipients come from six different countries and represent a variety of institutions. They are:
- Khushi Chhillar, University of Delhi, India
- Madjid Tehrani, Edinburgh Napier University, United Kingdom
- Muhammad Arif, Pakistani International Airlines (a government-owned airline), Pakistan
- Nikita Malik, University of Delhi, India
- Nikolas Gauder, Technical University of Munich, Germany
- Paul Louvel, IDEMIA (attending as an individual developer), France
- Sivakumar Natarajan, University of North Carolina Greensboro, United States
All recipients are actively engaging with OpenSSL in some capacity, and each made a compelling case for how attending the conference would benefit them and also have a positive impact on the OpenSSL project and beyond.
More ...Why we are excited about the OpenSSL Conference
Early bird registration for the first OpenSSL Conference is available until August 31. Now is the best time to register.
With over 90 talks, there’s something for everyone at the OpenSSL Conference in Prague from October 7–9. The OpenSSL Foundation will be presenting two talks:
- Matt Caswell, President of the Foundation, will speak on the Foundation’s mission and what we are doing to deliver on it.
- Jon Ericson, the Foundation’s Communities Manager, plans to discuss the state of the OpenSSL community.

Contributors to the OpenSSL Library (July 2025)
In July, 58 pull requests were approved for merge into the OpenSSL Library code base. There were also four people who contributed code for the first time:
- yzpgryx provided a fix to support the SM2 PEM format with matching tests.
- caolanm designated an unchanging structure to be constant.
- igus68 found a good first issue and fixed it. Before this fix, the OpenSSL cryptographic library would accept a certificate revocation list that was invalid according to the X.509 Public Key Infrastructure specification. Fun fact: Igor Ustinov represents the Individuals community on the Foundation Technical Advisory Committee and this is his first pull request. And he’s on a roll with another pull request that addresses an issue with the help wanted label.
- Saurabh825 corrected the order of options for the asn1parse command.
So far in the development cycle of OpenSSL 3.6, the plurality of changes come from developers paid by either the OpenSSL Corporation or Foundation. But individual contributions continue to make up a large proportion of commits (41%) and overall changes (28%). Additionally individual committers also have done 18.5% of reviews so far.
More ...OpenSSL Foundation endorses UN Open Source Principles

The UN Open Source Principles are a set of eight guidelines designed to promote collaboration and the adoption of open-source technologies within the UN and globally. The OpenSSL Foundation is proud to endorse these principles, which capture our existing ways of working and help raise awareness about the value of open source across industries, geographies, and communities.
The eight principles are:
More ...Sovereign Tech Fund Invests in OpenSSL

The OpenSSL Foundation is pleased to announce a €405,888 investment from the Sovereign Tech Fund to enhance timing side-channel resistance in the BIGNUM code and address a backlog of user-submitted GitHub issues.
While most computers are typically handling 64bit numbers, OpenSSL’s code works with much larger numbers, which we call BIGNUMs. Depending on the exact size of the BIGNUM, the amount of time taken to process these very large numbers can vary. These small timing variations can pose potential security concerns. This issue was first raised in July 2018, and we’ve continued to receive security reports about it over the years, most commonly from academic researchers. Although OpenSSL developers have fixed individual issues, we’ve been unable to tackle the underlying problem because of its complexity, competing priorities, and limited engineering resources.
More ...Early-bird registration is now open for the OpenSSL Conference 2025

Registration is now open for the inaugural OpenSSL Conference, taking place October 7-9, 2025, in Prague, Czech Republic. There is a discount for early registration, so now is the best time to secure your spot!
Join the global community of cryptographers, open-source innovators, security experts, and thought leaders who shape the future of secure communications. The OpenSSL Conference promises to be a landmark event, uniting diverse perspectives from across technical, enterprise, academic, and regulatory fields.
More ...The OpenSSL Foundation announces scholarship opportunities for the OpenSSL Conference

The OpenSSL Foundation serves individual developers, academics, nonprofits, and non-commercial distributions that work with OpenSSL. We are committed to ensuring that individuals from these communities are able to attend the inaugural OpenSSL Conference, taking place in Prague on October 7-9, 2025 and are pleased to provide a limited number of conference scholarships.
Scholarships are funded through the generosity of the Foundation’s donors and sponsors. We are especially grateful to the Code Protectors, whose annual support provides us with the means to undertake new initiatives like this one.
More ...Cryptocurrency added to donation options
We’re pleased to announce that the OpenSSL Foundation now accepts cryptocurrency donations through our giving partner, The Giving Block. This new option offers donors an easy and secure way to support our mission using Bitcoin, Ethereum, and many other digital assets. Donations can be made easily and securely through this form on our website.
The OpenSSL Foundation does not maintain its own cryptocurrency wallets but partners with The Giving Block to receive the cash equivalent of these donations. One added benefit of this partnership is that you may choose to donate to the OpenSSL Foundation with full anonymity – we will receive your gift but not any of your personal information. (Thank you to our first-ever cryptocurrency donor who made just such an anonymous gift on 6 July 2025!)
More ...The Features of 3.5: EVP_SKEY
This is the fifth in a series of posts about the features of OpenSSL 3.5. Its target audience is people who are curious about internet security, but who don’t recognize the acronyms in that list.
- QUIC server
- External QUIC library interface
- Post-quantum cryptography
- Hybrid ML-KEM in TLS v1.3
- EVP_SKEY
In this series we are explaining the acronyms used by the developers of OpenSSL. While it’s handy, necessary even, to have a shorthand for complicated cryptography concepts, that shorthand stands as a barrier for non-experts seeking to understand.
More ...The State of the OpenSSL Community (3.5)
Open source projects depend on a community of volunteers to submit and review features, bug fixes, documentation improvements and so on. OpenSSL has benefited from a core of dedicated contributors and has built up a robust community over the last decade. A lot more people have their eyes on OpenSSL since 2014, the year Heartbleed was discovered.
OpenSSL 3.5 was released earlier this year with a bunch of exciting features. Roughly a third of the commits came from people paid by either the OpenSSL Foundation or OpenSSL Corporation. The rest of the commits were submitted either by individuals or developers working for other companies. Jon Ericson, the OpenSSL communities manager, discussed the state of the community in a new video:
More ...There's still time to share your story
Recently we opened a short survey for people to share their OpenSSL stories. We’ve already heard from people who use OpenSSL to:
- Analyze QUIC traffic.
- Secure school cafeteria point of sale (POS) systems.
- Protect letters sent digitally to a printer before they are sent physically, on paper, via the postal system.
- Generate a JSON Web Token (JWT) from a PEM (Privacy Enhanced Mail) file without depending on a third party.
- Support software that depends on OpenSSL.
OpenSSL Foundation is hiring Software Engineer (C Developer)
Please note that we are no longer accepting new applications for this position.
OpenSSL Foundation is seeking a talented and motivated Software Engineer (C Developer) to contribute to the development and maintenance of the widely-used OpenSSL open-source cryptographic library.
More ...Foundation Business Advisory Committee special election
Currently there is no Small Business representative on the Foundation Business Advisory Committee (BAC), so the community voted to request a special election. In the interest of getting the representative in place as soon as possible, the nomination and voting periods will be shorter than usual.
Election timeline
- Now—Everyone interested in nominating or voting should join the small business group.
- June 11–June 25 (2 weeks)—Nominations and Candidate Vetting
- June 26–July 6 (11 days)—Voting
- July 7—Results Announcement
Please consider whether you will nominate yourself. This is your opportunity to participate in planning the future of OpenSSL.
More ...FLOSS/fund Backs the Future of Internet Security

Today we celebrate FLOSS/fund, which has made a $100,000 investment in the future of OpenSSL with a contribution to the OpenSSL Foundation. Established by Zerodha in 2024, FLOSS/fund was created with the bold vision of providing $1 million per year to free/libre and open source software projects globally. We are proud to be among the fund’s first tranche of recipients!
In his initial announcement of FLOSS/fund, Kailash Nadh, CTO of Zerodha, shared, “it makes perfect logical sense for a business that relies on FOSS to support it, directly or indirectly, when they freely tap into a global ecosystem of unlimited FOSS innovation—free in both cost and freedom. How many technology companies today could even exist without the massive amounts of FOSS they use?” Zerodha is also a proud supporter of the Open Source Pledge, a global initiative that encourages companies to financially support the open source projects they depend on.
More ...May Foundation BAC meeting minutes
Last week the Foundation Business Advisory Committee (BAC) met. Minutes can be found on the communities site. Key takeaways:
- The Foundation has been pursuing funding for some of the top
potential features for 3.6 and beyond as voted on by the
BAC:
- BIGNUM refactoring for constant-time
- Encrypted Client Hello (ECH)
- DTLS 1.3
- Backlog of Github issues and PRs
- Since 3.0, a number of OpenSSL forks have diverged for a variety of reasons. The BAC considered the various reasons for the forks how the OpenSSL project might support those use cases.
- The BAC considered creating a disaster recovery plan. For instance, what would happen if GitHub were no longer an appropriate platform for the project.
- The directors will consider a proposal for regular “open hours” sessions.
- Going forward, the Foundation BAC will meet in the last week of each month and alternate timezones.
Share your user story

If you’re reading this blog post, you probably don’t need us to tell you how essential, widespread, and important the OpenSSL Library is. While our open source model means that everyone is freely able to use these tools, it also means we here at the OpenSSL Foundation don’t actually know all the great stories of how these tools are being used.
We’re looking for real stories of how the OpenSSL Library benefits your end users.
More ...Deadline Extended: More Time to Submit Your Proposal for the OpenSSL Conference 2025

The OpenSSL Conference 2025 is extending its Call for Papers (CFP) deadline to June 22, 2025.
We understand that the best proposals often come from teams deep in the trenches of real-world security work. You now have additional time to craft and submit the talk, panel, or workshop that challenges assumptions, advances cryptographic innovation, drives and shapes the future of secure communications.
More ...My week at ICMC 2025 with the OpenSSL Foundation: Faces, PQC, and Real-World Challenges
Nicola Tuveri is a long-term contributor to OpenSSL and a member of both the Foundation’s Business Advisory Committee and Technical Advisory Committee. The Foundation sponsored his attendance at ICMC 2025 and here are his reflections on the experience.
Early last month, I had the pleasure of attending the International Cryptographic Module Conference (ICMC) in Toronto. As an attendee, my mission was simple: reconnect, listen, and learn. And ICMC delivered on all fronts.
More ...The OpenSSL Corporation and the OpenSSL Foundation Launch Distinguished Contributor Awards with OpenSSL 3.5 Honorees
The OpenSSL Corporation and the OpenSSL Foundation are launching the Distinguished Contributor Awards, a new programme formally recognising exceptional technical contributions to each OpenSSL Library release. These awards highlight individuals who drive critical advancements and demonstrate technical leadership in the evolution of the OpenSSL Library.
More ...Call for speakers at the inaugural OpenSSL Conference
The first OpenSSL Conference will take place October 7–9, 2025 in Prague. It will be an excellent opportunity to learn more about OpenSSL. Talks will range from technical discussions of cryptography to open source communities to practical guidance for internet security.
More to the point, it’s a great opportunity to speak about these topics. If you have expertise in a topic related to OpenSSL, please consider applying to be a speaker. In addition to the unique opportunity to address the OpenSSL community, speakers will receive a complimentary conference pass.
More ...Technical Advisory Committees Election Results
The OpenSSL Corporation and the OpenSSL Foundation certify the results of the Technical Advisory Committee (TAC) elections. After a thorough nomination and voting process, the OpenSSL community has selected a group of distinguished individuals to provide guidance and advice to the OpenSSL Library.
More ...RSA Conference: New perspectives
Our communities manager, Jon Ericson, was at the RSA Conference. Below are his reflections on the conference as a whole:
I attended several of the keynotes, including a performance by rapper Common, Ron Howard getting interviewed by his daughter Bryce Dallas Howard and Magic Johnson doing Magic Johnson things. More on topic for a security conference was From Gamer to Leader: How to Build Resilient Cyber Teams which suggested that people who play video games would be good candidates for becoming security professionals.
More ...RSA Conference Day 2: A bit of history
Our communities manager, Jon Ericson, is at the RSA Conference. Below are his reflections on the second day of the conference:
The Cryptographers’ Panel

From talking with people who have come to RSA many times, the highlight of the conference every year is The Cryptographers’ Panel, which includes luminaries in the field such as Whitfield Diffie, who pioneered public key cryptography and Adi Shamir, who co-developed the RSA cryptosystem. This year the topics included cryptocurrency, blockchain technology, AI and post-quantum cryptography. What I found notable was the level of disagreement on all sorts of questions:
More ...RSA Conference Day 1: The Human Factor
Our communities manager, Jon Ericson, is at the RSA Conference. Below are his reflections on the first day of the conference:
When I arrived at Moscone Center, where the RSA Conference is held, the first thing I did was connect to the wireless network. That required me to view this disclaimer:

In some sense the audience of the RSA Conference ought to know how to manage their network risk. Personally I took comfort knowing that all the websites I connect to use HTTPS. But as I attended sessions, it occurred to me that most of the security risks we face are not technological, per se.
More ...The Features of 3.5: Hybrid ML-KEM
This is the fourth in a series of posts about the features of OpenSSL 3.5. Its target audience is people who are curious about internet security, but who don’t recognize the acronyms in that list.
- QUIC server
- External QUIC library interface
- Post-quantum cryptography
- Hybrid ML-KEM in TLS v1.3
- EVP_SKEY
Previously we discussed how quantum computing represents a threat to the cryptographic systems that secure digital communication. In order to ensure privacy and well into the future, we need to find new ways of encrypting data.The ML in ML-KEM is a new type of public key designed to do just that. In the field of cryptography, ML stands for “module lattice”1 and it’s used in one method standardized by the National Institute of Standards and Technology (NIST) for encrypting keys.
More ...Have Your Say! Vote Now in the Technical Advisory Committee Elections and Support Your Community
Thank you to everyone who registered and to those who took the extra step to nominate candidates for the Technical Advisory Committees (TACs) of the OpenSSL Corporation and the OpenSSL Foundation.
We are now at the final step—voting. Your participation in this phase is essential to bring the process to completion and ensure the strength of our shared governance.
Election Timeline
Start Date: April 28, 2025 at 12:00pm UTC
Deadline for Voting: May 11, 2025 at 12:00pm UTC
More ...The Foundation is going to the RSA Conference
Every year the RSA Conference happens in San Francisco, California. This year (April 28–May 1, 2025) the OpenSSL Foundation will be represented by the Communities Manager, Jon Ericson.
More ...The Features of 3.5: Post-quantum cryptography
This is the third in a series of posts about the features of OpenSSL 3.5. Its target audience is people who are curious about internet security, but who don’t recognize the acronyms in that list.
- QUIC server
- External QUIC library interface
- Post-quantum cryptography
- Hybrid ML-KEM in TLS v1.3
- EVP_SKEY
In order to explain “Hybrid ML-KEM in TLS v1.3” we need to start with the way internet security works today and how a new type of computer could change everything. The first post in this series introduced Transport Layer Security (TLS), which encodes messages sent across the internet. (v1.3 is the most recent version of the protocol.) Because of the way the internet works, you can’t necessarily control who can access the data you send and receive. Just as you lock your front door in order to keep strangers out, you need to encrypt messages to prevent strangers on the internet from reading them. In order to grant access to people you trust, you have to give them the key that opens the door.
More ...ICMC Recap
Foundation staff Tomáš Mráz and Amy Parker were attendees at last week’s International Cryptographic Module Conference (ICMC) and PQ Cyber Day, which brought together industry experts, government representatives, and researchers from around the globe. The timing was just right, as the final release of OpenSSL 3.5 went live during the conference and includes support for PQC algorithms ML-KEM, ML-DSA, and SLH-DSA.
PQ Cyber Day was a full-day of sessions focused on the opportunities and challenges for post-quantum computing migration. Speakers from the Canadian Centre for Cyber Security (CCCS) and the National Institute for Standards and Technology (NIST) spoke about the “Harvest Now, Decrypt Later” threat, the need for cryptographic agility, and the fact that cybersecurity is not just an IT issue but a shared responsibility that requires buy-in and investment from the top. A variety of industry speakers shared their experiences with migrating cryptographic inventories, code signing, and hardware security modules to the NIST PQC standards.
More ...Nomination Deadline Extended: Technical Advisory Committees
The nomination period for the Technical Advisory Committees (TACs) has been extended. The new deadline is Sunday, April 27, 2025.
Take advantage of the extended timeline to submit thoughtful nominations — and play an active role in shaping the future of the OpenSSL Library. Your voice matters!
More ...OpenSSL 3.5 Final Release - Live
The final release of OpenSSL 3.5 is now live. We would like to thank all those who contributed to the OpenSSL 3.5 release, without whom the OpenSSL Library would not be possible.
More ...Join Us at the OpenSSL Conference in Prague – October 7 to 9, 2025 - Share Your Expertise and Shape the Future of Secure Communications

The OpenSSL Corporation and the OpenSSL Foundation are pleased to announce the OpenSSL Conference 2025, taking place from October 7 to 9, 2025, in the historic city of Prague, Czech Republic. This premier event brings together a global community of cryptography experts, legal professionals, and open-source enthusiasts dedicated to advancing cryptography and secure communications for three days of in-depth discussions, insights, and networking.
More ...The Features of 3.5: External QUIC library interface
This is the second in a series of posts about the features of OpenSSL 3.5. Its target audience is people who are curious about internet security, but who don’t recognize the acronyms in that list.
- QUIC server
- External QUIC library interface
- Post-quantum cryptography
- Hybrid ML-KEM in TLS v1.3
- EVP_SKEY
When software developers want to avoid reinventing the wheel, they look for a software library, such as OpenSSL.1 Software libraries function like physical libraries in that people may freely borrow material for their own use. (Unlike a physical library, you don’t have to return code for someone else to use it!) Libraries have other books, such as encyclopedias and reference material, that aren’t allowed to be used outside of the library. In the same way, software libraries have code that’s not intended for external use, so there must be a way for programmers to know what can be reused. An API (application programming interface) defines what’s safe to borrow.
More ...Thank You for Joining Our Live Q&A Session on Technical Advisory Committees
On March 24 and 25, 2025, we hosted two live Q&A sessions to discuss the formation and role of the new Technical Advisory Committees (TACs) concerning the OpenSSL Library. These sessions featured:
- Tim Hudson, President of the OpenSSL Corporation (Session 1)
- Matt Caswell, President of the OpenSSL Foundation (Sessions 1 and 2)
- Anton Arapov, Operations Director of the OpenSSL Corporation (Session 2)
- Hana Andersen, Marcom Manager of the OpenSSL Corporation (both sessions)
- Moderated by Kajal Sapkota
These interactive webinars offered our community the opportunity to ask questions and better understand the purpose and structure of the TACs.
More ...OpenSSL at ICMC 2025: Join Us in Toronto!
The OpenSSL Foundation is happy to announce our participation in the PQ Cyber Day and International Cryptographic Module Conference (ICMC), taking place in Toronto on April 7-10, 2025. ICMC is a premier event in the field of cryptographic modules, compliance, and security, bringing together industry experts, government representatives, and researchers from around the globe. The PQ Cyber Day is an associated one day special-focus event happening just before ICMC.
More ...Do Not Miss Our Technical Advisory Committee Q&A Sessions - Get Involved!
Thank you to everyone who registered and to those who went the extra mile to nominate candidates for the Technical Advisory Committees of the OpenSSL Corporation and OpenSSL Foundation.
More ...A prime day for pie
Two members of the Foundation staff are excited because today is Pi Day while the other three are saying to themselves, “What in the world is Pi Day?” If you are asking the same question, here are some clues:
Hint 1
The two staff who know about Pi Day are American.Hint 2
Dates in the United States are usually written with the month first: "MM/DD".Hint 3
Today is 14 March.Solution
To an American, today is 3/14 or the first three digits of π.Pi Day is a surprisingly big deal. For some it’s an excuse to eat pie. (Get it?) For others it’s a day for exploring an irrational number. The Massachusetts Institute of Technology (MIT) sends out college admission decisions on Pi Day. Perhaps more relevant to OpenSSL, UNESCO has declared 14 March as the International Day of Mathematics. Pi gets the name recognition, but another mathematical concept, prime numbers, plays an outsized role in securing communication over the internet.
More ...Join Us in Forming the Technical Advisory Committees (TACs)
The OpenSSL Corporation (primarily focused on commercial communities) and the OpenSSL Foundation (primarily focused on non-commercial communities) are pleased to announce the formation of the Technical Advisory Committees (TACs) to provide expert guidance and strategic direction for our technical initiatives. This marks a significant milestone, and we need dedicated individuals to help shape their future.
More ...The Features of 3.5: QUIC server
This is the first in a series of post about the features of OpenSSL 3.5. Its target audience is people who are curious about internet security, but who don’t recognize the acronyms in that list.
- QUIC server
- External QUIC library interface
- Post-quantum cryptography
- Hybrid ML-KEM in TLS v1.3
- EVP_SKEY
It can be helpful to think of the internet as a series of agreements about how computers talk to each other. Those agreements are called protocols and they can be mixed and matched according to the purpose of the communication. Protocols can be layered on top of each other with each protocol depending on the layer below and supporting the layer above.
More ...Foundation Board of Directors election
The Members of the OpenSSL Foundation recently held an election for a seat on the Board of Directors that expired at the beginning of March. We are pleased to announce that Richard Levitte has been re-elected for another 3-year term.
Directors may be officers, In a meeting after the election, the board decided Richard will fill the role of Secretary. Tomas Mraz, who previously held that office, will now be the Foundation’s Treasurer.
More ...Announcing the Code Protectors

The OpenSSL Library is one of the world’s best known cryptographic libraries. Used by countless companies around the world, it provides data privacy and security to millions of end users. Today, we are announcing a new way for companies who value this vital internet infrastructure to support us: the Code Protectors sponsorship program.
The Code Protectors program provides companies with a range of sponsorship benefits commensurate with their level of support. We offer five sponsorship levels, from the “pay what you can” Copper level to the Platinum level of $50,000 or more.
More ...Foundation face-2-face meeting
At the end of January and the beginning of February the Foundation team were able to get together for a series of face-2-face meetings. The Foundation team are normally physically distributed around the globe, so getting together in person really makes a difference. These face-2-face meetings were particularly significant since it was the first time that our newest recruits Amy Parker and Jon Ericson had attended one.

Our first stop was in Brno in the Czech Republic where we were kindly hosted by our colleagues in the OpenSSL Corporation in their new office. We took the opportunity while we were there to have some joint sessions with the Corporation.
More ...Foundation Technical Advisory Committee election timeline
Following the new governance plan, the OpenSSL Foundation invites members of the OpenSSL community to nominate themselves for the Foundation Technical Advisory Committee (TAC). As the name implies, this committee will advise the Foundation on technical aspects of the OpenSSL project. Together with the Corporation TAC, it replaces the OpenSSL Technical Committee (OTC).
As with the BAC nomination process, there will be 6 seats designated for these 6 sub-communities:
Nominees must be prepared to spend up to 10% of work hours on committee duties, be able to attend an in-person meeting in Europe, and write a brief statement about how they will represent their community. Based on what we learned from the BAC elections we’re giving potential nominees a bit more time to prepare.
More ...Flint & Silicon interview
The Flint & Silicon podcast features interviews with grant managers, policymakers, technologists and others about how we can all work together to improve society. In the latest episode, Amy Parker, Chief Funding Officer, speaks about fundraising, both from the perspective of traditional nonprofits and within the open source ecosystem.
Watch the episode here, or explore other ways to listen.
For further information about some of the things Amy mentions in the interview, check out these links:
More ...A new perspective on fundraising
The FOSDEM conference is well known in the free and open source software community for its developer rooms (devrooms) where teams can meet, hack, and present on their latest projects. Devrooms are themed around topics such as Security, Quantum Computing, and Data Analytics. This year, for the first time, FOSDEM also included a “Funding the Free and Open Source Software (FOSS) Ecosystem” devroom, and the OpenSSL Foundation was proud to participate.

What we learned at FOSDEM 2025
FOSDEM is the world’s largest open source conference that’s held every year at the ULB Solbosch Campus in Brussels, Belgium. So, of course the OpenSSL Foundation was there. FOSDEM is a free conference that’s entirely created and run by volunteers. One member of our team, Tomas Mraz, was a co-organizer of the Security Devroom. Amy Parker volunteered for a shift at the Information Desk, where she sold t-shirts and accepted donations from attendees who wanted to support FOSDEM.
More ...The Foundation at FOSDEM 2025
As we mentioned earlier this month the OpenSSL Foundation is at FOSDEM:

This photo is from the welcome talk and is missing Amy Parker, who is putting the final touches on her talk tomorrow.
Matt, Richard and Tomáš can be found in and around the security devroom, while Jon is stationed in the community room. We should be visible in our hunter green shirts.
More ...Initial meeting of the Business Advisory Committee
In July, we announced a new governance structure that includes an elected Business Advisory Committee (BAC) for the OpenSSL Foundation. After an election and a runnoff the members of the Foundation BAC are:
- Academics – Nicola Tuveri (Tampere University)
- Committers – Paul Dale (Oracle)
- Distributions – Tie between Dmitry Belyavsky (Red Hat)
- Individuals – Randall Becker
- Large Businesses – Tim Chevalier (NetApp)
- Small Businesses – vacant seat
Their first meeting was today. In the interest of transparency, the meeting minutes are public. The Foundation staff organized the kickoff meeting, but the expectation is that the committee will self-organize with help from staff, as needed. Jon Ericson, as the newly hired communities manager, will be the liaison between the Foundation and the BAC.
More ...OpenSSL Position and Plans on Private Key Formats for the ML-KEM and ML-DSA Post-quantum (PQ) Algorithms
The anticipated future arrival of cryptographically relevant quantum computers (CRQCs), that could undermine the algorithms that underlie the currently most widely used public key algorithms (ECDHE, ECDSA, DH and RSA), has led to the development and recent standardisation of new “post-quantum” (PQ) algorithms, that are believed to not be vulnerable to CRQC attack.
Two of the first algorithms standardized are ML-KEM (for key agreement) and ML-DSA (for digital signatures). These algorithms are standardized by NIST in FIPS 203 and FIPS 204. These define the algorithm parameters and how to correctly perform the necessary mathematical operations, but do not define such details as data formats for public and private keys. Those details were left to other standards organisations, such as the IETF.
More ...Introducing Jon Ericson
From the very beginning of the project, OpenSSL has depended on a community of experts to enable secure and private communication. It’s safe to say that without volunteers contributing code, tests and documentation, we wouldn’t have the modern internet. In order to preserve and grow that ecosystem, the OpenSSL Foundation has brought in Jon Ericson as its first Communities Manager.
Jon began his programming career as an intern at the US National Weather Service where he designed software to test instruments for the Automated Surface Observing System (ASOS). He continued as a programmer at the Jet Propulsion Laboratory (JPL) with the Shuttle Radar Topography Mission (SRTM) ground-data team. When that project ended, he managed data processing for the Tropospheric Emission Spectrometer (TES) mission which collected global atmospheric data from heliosynchronous orbit. Along the way he participated in open source projects such as Perl and Emacs via Usenet groups and mailing lists.
More ...Connect with us at FOSDEM
The OpenSSL Foundation will be attending FOSDEM in Brussels, Belgium on 1-2 February 2025, and we’d like to connect with you!
The Free and Open Source Developers’ European Meeting (FOSDEM) is a volunteer-organized event to promote the widespread use of free and open source software. The conference includes 1,001 events across two days, taking place in 40 rooms on the ULB Solbosch Campus. There is no fee to participate and attend.
More ...OpenSSL Foundation publishes first ever annual report
The OpenSSL Foundation is pleased to share its Annual Report for fiscal year 2024, covering the period of August 1, 2023 through July 31, 2024. This public document is a first for the Foundation, reflecting a renewed commitment to transparency with our communities and the sponsors and donors whose contributions provide critical financial support.
One year ago, we celebrated the 25th anniversary of OpenSSL, marking the release of version 0.9.1c on December 23, 1998, and it seemed fitting to share this Annual Report today, on OpenSSL’s 26th birthday. So much has changed over those 26 years, but our reliance on our community of committers, contributors, and funders has not. We greatly appreciate the many contributions of many types that keep OpenSSL strong and secure and hope you enjoy reading about all that we achieved together.
More ...Foundation BAC Distributions seat
As previously communicated the recent election for the Distributions seat on the Foundation BAC resulted in a tie between Dmitry Belyavsky (Red Hat) and John Haxby (Oracle). As a result we will be re-running this election in early January with just these two candidates. Voting will open on 3rd January 2025 and will close on 10th January 2025.
The “Distributions” community includes maintainers of operating systems or significant packages that integrate OpenSSL Foundation and OpenSSL Corporation projects. If you are involved in an OpenSSL distribution then we encourage you to sign up to the community and vote in the second round of the election in January.
More ...Announcing the Results of the Business Advisory Committee Elections
Upon certification of the election results by the Election Committee, the OpenSSL Foundation and the OpenSSL Corporation are pleased to announce the official results of the Business Advisory Committee (BAC) elections. After a thorough nomination and voting process, the OpenSSL community has selected a group of distinguished individuals to provide guidance and advice to OpenSSL.
Newly Elected Members
The following candidates have been elected to serve on the Business Advisory Committee:
OpenSSL Foundation BAC Members
More ...Re-opening donation opportunities to OpenSSL Foundation
The OpenSSL Foundation is pleased to announce that we are reopening the opportunity for individuals to financially support our work through donations on Github Sponsors. Individual contributions of time, expertise, and financial support have always been critical to our ability to keep improving the OpenSSL software library, and we are excited to once again welcome financial contributions at all levels.
More ...Business Advisory Committees Elections Are Now Open - Vote for Your Community Representative
Thank you to everyone who registered, as well as those who took the extra step to nominate candidates, for the Business Advisory Committees of the OpenSSL Foundation and OpenSSL Corporation. We are now at the final step - voting - which is essential to complete the process.
Start Date: December 5, 2024
Deadline for Voting: December 15, 2024 11:59pm Pacific Time (US/ Canada)
Election Committee
The Election Committee is composed of the directors of the OpenSSL Foundation and the OpenSSL Corporation. This marks the first inaugural Election Committee, tasked with overseeing and managing the election processes across various communities. The committee is dedicated to ensuring that voting is conducted fairly, transparently, and in alignment with the established rules and procedures.
More ...Nominations Remain Open Until Wednesday, December 4, 2024 - Based on Your Feedback!
Thank you to everyone who attended our Q&A sessions about the formation of Business Advisory Committees. We received valuable input from our communities, including requests to allow more time for nominations.
We have heard you, and we would like to announce that:
- The nomination period has been extended until Wednesday, December 4, 2024.
- The election period starts on Thursday, December 5, 2024 and ends on Sunday, December 15, 2024. You can change your vote up to the end of the election period.
This extension provides additional time to ensure everyone has the opportunity to nominate the individuals who can best represent the community’ s view and needs.
More ...Websites mirrors
To align with our mission, we have provisioned mirrors for our websites, hosted through our chosen CDN vendor:
- https://mirror.openssl.org
- https://mirror.openssl-mission.org
- https://mirror.openssl-library.org
- https://mirror.openssl-foundation.org
- https://mirror.openssl-corporation.org
- https://mirror.openssl-projects.org
- https://mirror.openssl-conference.org
These mirrors are accessible in locations where our original websites might be blocked.
OpenSSL Holds Inaugural OpenSSL Projects Meeting
The OpenSSL Foundation and the OpenSSL Corporation are pleased to announce the successful conclusion of the inaugural meeting with Bouncy Castle and cryptlib, two newly integrated projects under the OpenSSL Mission. This meeting represents a pivotal step in the evolution of OpenSSL’s governance structure, as outlined in the recent organizational changes, and reflects a deepened commitment to advancing privacy and security.
Bouncy Castle and cryptlib reaffirmed their alignment with the OpenSSL Mission and Values. The discussions focused on their involvement with OpenSSL Projects, and the specifics of how they will leverage the OpenSSL Foundation and the OpenSSL Corporation for their particular needs, such as shared engineering resources or access to performance test infrastructure.
More ...OpenSSL Business Advisory Committee Q&A Session
Thank you to everyone who registered, as well as to those who took the extra step to nominate candidates, for the Business Advisory Committees of the OpenSSL Foundation and OpenSSL Corporation.
We invite you to attend our Q&A session, designed to address your questions. We encourage you to join the session and gain valuable insights about the nomination and election process, the role of the Business Advisory Committee, and how you can participate in shaping OpenSSL’s future.
More ...Upcoming Webinar - Working with X.509 Keys and Certificates
Advance Your Skills in X.509 Certificate Management with OpenSSL
- Date: Nov 21, 2024
- Time: 04:00 PM Eastern Time (US and Canada)
- Duration: 1 hour
- Location: Online Webinar (link to be provided upon registration)
- Register Here
Are you looking to deepen your understanding of X.509 keys and certificates or sharpen your command-line skills?
Join us for a comprehensive webinar on X.509 certificate management led by Viktor Dukhovni, an OpenSSL Software Engineer. This session covers essential concepts and hands-on techniques using OpenSSL’s command-line tools.
More ...OpenSSL Forms Business Advisory Committees - Shape the Future - Join Now!
The OpenSSL Foundation (primarily focused on non-commercial communities) and the OpenSSL Corporation (primarily focused on commercial communities) are pleased to announce the formation of Business Advisory Committees (BAC), inviting our communities - Distributions, Committers, Small Businesses, Large Businesses, Individuals, and Academics - to actively engage in shaping the future of OpenSSL. These advisory bodies are critical in enhancing our governance structure, ensuring that the decisions reflect the diverse stakeholders involved and that our Mission and Values stay aligned with the community’s needs.
More ...OpenSSL 3.4 Final Release Live
The final release of OpenSSL 3.4 is now live. We would like to thank all those who contributed to the OpenSSL 3.4 release, without whom OpenSSL would not be possible.
OpenSSL delivers the following significant new features:
- Support for Integrity only cipher suites (RFC 9150)
- JITTER RNG support via statically linked jitterentropy library
- RFC 5755 Attribute Certificate support
- FIPS indicators in support of FIPS 140-3 validation
- Improved Base64 BIO input handling and error reporting
- XOF Digest size reporting improvements
- Windows Registry key-based directory lookup
- Support for several X509v3 extensions
- Support for position independent executables in the openssl app to support address space layout randomization
Please see the CHANGES.md file in the release for a full list of changes since OpenSSL 3.3
More ...OpenSSL is hiring Communities Manager
Please note that we are no longer accepting new applications for this position.
OpenSSL is hiring for a Communities Manager to join our team.
More ...Introducing Amy Parker
OpenSSL welcomes Amy Parker as the newest member of the OpenSSL Foundation team. Amy joins us in the newly created position of Chief Funding Officer, a fundraising role focused on revenue generation through corporate sponsorship and other charitable/non-commercial contributions. Funds raised will help the Foundation continue to deliver on its mission of providing security and privacy tools to everyone, everywhere.
A strategic leader with more than twenty years of senior-level fundraising experience, Amy has worked for prestigious educational and cultural institutions including the Wikimedia Foundation, Smithsonian Institution, The New York Public Library, and the University of North Carolina at Chapel Hill. She has been part of several record-setting fundraising campaigns, including the Smithsonian’s first-ever comprehensive campaign, which raised over $1.8 billion, and the $2 billion Carolina First Campaign, which was one of the 5 largest campaigns in US higher education at the time.
More ...OpenSSL 3.4 beta released
OpenSSL 3.4 beta 1 has now been made available.
Our beta releases are considered feature complete for the release, meaning that between now and the final release, only bug fixes are expected (if any). Notable features of this release are available in NEWS.md within the source tarball.
Beta releases are provided to our communities for testing and feedback purposes. If you use OpenSSL, and particularly if you intend to upgrade to OpenSSL 3.4 when it is released, we strongly encourage you to download this beta release, and test it within whatever quality control mechanisms you have, providing feedback via our GitHub issue page at http://github.com/openssl/openssl/issues, so that we can address any shortcomings prior to the final release
More ...OpenSSL Corporation's Silver Sponsorship at ICMC 2024 - A Retrospective
OpenSSL Corporation’s participation as a Silver Sponsor at the International Cryptographic Module Conference (ICMC) 18th - 20th September 2024 marked an important milestone in our continued commitment to advancing cryptographic technologies. As a critical player in secure communication, OpenSSL’s involvement highlighted our dedication to fostering collaboration, innovation, and security within the cryptographic community.
ICMC 2024 provided a valuable platform for industry leaders to engage in key discussions surrounding cryptographic standards, challenges, and innovations. Through our sponsorship, OpenSSL contributed to critical dialogues on post-quantum cryptography, regulatory compliance, and developing secure, open-source cryptographic solutions.
More ...Lightship Security Partnership with OpenSSL
OpenSSL is sharing Lightship Security’s latest press release, highlighting the new partnership with the OpenSSL Corporation. Read the full release below:
Lightship Security, an Applus+ Laboratories company and a leading cryptographic security test lab, announces its agreement with the OpenSSL Corporation to provide FIPS 140-3 validation services for the OpenSSL cryptographic library.
The OpenSSL Corporation provides commercial support for users of the OpenSSL Library, a critical component of secure communications in enterprise technologies.
More ...Post-Quantum Algorithms in OpenSSL
Recently NIST published a number of post-quantum algorithm standards (ML-KEM, ML-DSA, and SLH-DSA). With these new NIST publications, OpenSSL is now prepared for implementation.
We’ve recently been receiving a lot of questions about these new standards so we wanted to make our position clear:
- We intend to implement support for these algorithms in our providers in a future version of OpenSSL
- We are currently putting together our project plans for this, stay tuned for more information regarding timeline
- We invite qualified and skilled individuals to help us implement these algorithms and integrate them into OpenSSL in accordance with our standards and policies.
From early 2022 a research project made available a test vehicle enabling TLS1.3 and X.509 support for many pre-standard and other experimental post-quantum algorithms via the OpenSSL provider interface, called oqs-provider. Its primary author and maintainer (Michael Baentsch) has now joined the OpenSSL team with the goal to support an efficient, secure, smooth and seamless integration of the now standardised post-quantum algorithms from NIST into the OpenSSL code base. Many lessons learnt from the process of building and integrating oqs-provider into downstream applications will be applied to this process.
More ...OpenSSL 3.4 alpha released
OpenSSL 3.4 alpha 1 has now been made available.
Our Alpha releases are considered feature complete for the release, meaning that between now and the final release, only bug fixes are expected (if any). Notable features of this release are available in CHANGES.md within the source tarball.
Alpha releases are provided to our communities for testing and feedback purposes. If you use OpenSSL, and particularly if you intend to upgrade to OpenSSL 3.4 when it is released, we strongly encourage you to download this alpha release, and test it within whatever quality control mechanisms you have, providing feedback via our GitHub issue page at http://github.com/openssl/openssl/issues, so that we can address any shortcomings prior to the final release
More ...OpenSSL considering TLS 1.0/1.1 deprecation
Recently, OpenSSL proposed the deprecation of TLS 1.0/1.1 and solicited community feedback on the idea.
Feedback on the proposal was generally split down the middle, with half of the respondents indicating immediate depreciation with near-term removal was acceptable, while the remainder of the respondents with affirmative opinions noted that they represent, or know of products whose environment disallowed updating to TLS1.2 or later, and would need to re-enable the deprecated features for the foreseeable future.
More ...Join Our Webinar on Debugging OpenSSL Applications
Debugging is a crucial aspect of developing and maintaining reliable software. However, debugging can become particularly challenging when applications incorporate diverse and complex components like OpenSSL. This webinar is designed to help you navigate these complexities.
Webinar Details
Date: September 11, 2024
Time: 09:00 AM Pacific Time (US and Canada)
Platform: Zoom
Topic: Debugging OpenSSL Applications
Registration Link: Click here to register
What to Expect
- Internal Debugging Tools: Learn about the facilities OpenSSL provides to help you gain visibility into its internal behavior, allowing for more effective troubleshooting.
- External Diagnostic Tools: Explore additional tools that can be integrated with OpenSSL to diagnose and resolve more intricate issues.
For professionals dealing with OpenSSL, mastering these debugging techniques is essential to ensuring the stability and security of their applications.
More ...Join OpenSSL at the ICMC 2024 - Visit Our Exhibit Booth!
OpenSSL is pleased to announce its participation as a Silver Sponsor at the upcoming International Cryptographic Module Conference (ICMC) 2024, taking place from 18th to 20th September. Visit our booth and attend our presentations to discover how we can help each other.
Event Details
Conference Name: International Cryptographic Module Conference
Dates: 18th - 20th September 2024
Location: DoubleTree by Hilton, San Jose, California
Our Booth Number: 102
OpenSSL 3.4 Alpha release approaching
The freeze date for OpenSSL 3.4 Alpha is rapidly approaching.
Alpha freeze approaching
The freeze date for OpenSSL 3.4 Alpha is rapidly approaching. Planned features are viewable on our 3.4 Planning page. If you have a feature on the planning page, please ensure that your associated PRs are posted, reviewed, and merged prior to the freeze date (Friday, Aug 30, 2024), or it will be postponed until the next release.
More ...New Governance Structure and New Projects under the Mission
As part of our ongoing journey, OpenSSL is evolving to provide more opportunities for engagement that more effectively align with our mission statement and promote our values. OpenSSL is implementing various mechanisms to foster greater community involvement and enable our communities to play a key and active role in the decision-making process.
New Governance Framework
OpenSSL has two independent, co-equal organizations to support the OpenSSL Mission:
- The OpenSSL Foundation primarily focuses on non-commercial communities.
- The OpenSSL Corporation primarily focuses on commercial communities.
This balanced approach ensures that both entities can operate independently and make decisions autonomously.
More ...OpenSSL is hiring - Fundraiser
Note that this position has now been filled and we are no longer accepting applications
OpenSSL is hiring for a Fundraiser to join our team
We are seeking a Fundraiser to join our team. As a Fundraiser at OpenSSL, you will play a vital role in sustaining critical components of internet infrastructure that enable secure communications around the world. In addition to your fundraising role, you must align with and uphold our core values and mission in your every day professional activities. This role will require you to have strong networks and relationships with our various sponsors, customers and communities in order to help us identify and bring on board new sponsors for our project as well as maintain our existing ones. You will also hold significant responsibility for developing our sponsorship and fundraising program in order to ensure that our sponsors are getting good value from their engagement with us whilst at the same time maximizing the resources available to OpenSSL to further develop and expand.
More ...Meet with OpenSSL at RSA Conference 2024
This year, OpenSSL will be attending RSA Conference 2024, one of the world’s largest cybersecurity events. Throughout May 6-9 in San Francisco, we are seeking to engage with our communities at RSA to better understand their needs and problems.
More ...Face-to-Face 2024 Australia
The OpenSSL Project has returned from spending a week in February sequestered in the beautiful Australian outback discussing the past, current, and future state of the project. This in-person meeting brought together the project’s paid resources and the management committee. Our goal for this meeting was to chart the course for OpenSSL’s future, tackle current challenges, and note our collective achievements. Three project members were unable to participate in person and joined the meetings remotely.
More ...Celebrating 25 Years of OpenSSL
We are pleased to announce that we have successfully distributed nearly 100 limited edition T-shirts commemorating the 25th anniversary of OpenSSL’s existence.
We appreciate the support of all our communities, users, individual contributors and support customers, without which we would not be able to continue our mission and deliver on our open source values. These continue to drive the success and evolution of OpenSSL, and we couldn’t be more appreciative.
More ...OpenSSL at FOSDEM 24
This year, we had the privilege of participating in FOSDEM for the first time. This offered us an opportunity to engage with the open source community at the conference, share our insights, and learn from the vast pool of knowledge that FOSDEM brings together.

FOSDEM, short for Free and Open Source Software Developers’ European Meeting, is an event that brings together thousands of open source developers, enthusiasts, and professionals from around the world. It’s a festival of knowledge, with workshops, talks, and sessions covering a myriad of topics from software development and security to hardware innovation and beyond.
More ...OpenSSL Working Group Update
As many of you are aware we have undergone a lot of internal organisation changes within the OpenSSL Project in the last couple of years, one of the key changes being the introduction of the OpenSSL Working Group.
In the February 2023 face-to-face meeting we decided to create the OpenSSL Working Group in an effort to be more efficient at addressing and executing on decisions made.
The WG was formed as an initiative to include more people into the OpenSSL decision making process and organize a place where OMC members, engineering, management, paid team members, and invited third parties all meet together and tackle urgent issues together and in a timely manner.
More ...NetApp and OpenSSL: Teaming Up for More Secure Internet
Exciting news in the world of online security! NetApp, an intelligent data infrastructure company, is now a Gold Sponsor of OpenSSL, showing their strong support for making the internet a safer place for everyone.
NetApp’s sponsorship brings valuable resources to OpenSSL, enabling the project to accelerate development, conduct thorough security audits, and ensure ongoing maintenance and support. In return, NetApp gains access to cutting-edge cryptographic technologies, contributing to the enhancement of its own security solutions and reinforcing its position as a leader in data management.
More ...OpenSSL's Official Youtube Channel
We are thrilled to announce a major leap forward in our efforts to connect with the community and share valuable insights—OpenSSL now has its own YouTube channel! As a significant milestone in our commitment to transparency, education, and open-source collaboration, this channel will serve as a hub for engaging content, tutorials, and updates straight from the heart of OpenSSL.
What to Expect:
Tutorial Series: Get ready for in-depth tutorials covering a wide range of topics, from OpenSSL basics to advanced usage scenarios. Whether you’re a seasoned developer or just starting, our tutorials will cater to all skill levels.
More ...OpenSSL 25 Year Anniversary T-Shirt Giveaway
We are thrilled to announce a special celebration in honor of OpenSSL’s 25th anniversary! Two and a half decades of commitment to security, reliability, and open-source collaboration have made OpenSSL an indispensable tool in the world of digital communication.
To express our gratitude to the incredible community that has supported us throughout the years, we are hosting an exclusive T-Shirt Giveaway! The first 75 people to participate will receive a limited edition OpenSSL 25th-anniversary T-shirt as a token of our appreciation.
More ...OpenSSL Project Update at ICMC 23

As you may know the OpenSSL Project recently attended ICMC 23 where we were given the opportunity to update our peers about the rapid fundamental changes the project has gone through in 2023.
To summarize here are the key takeaways from our presentation:
More ...OpenSSL at ICMC 23
As a part of our mission to be more open and engaged with our community, OpenSSL is pleased to announce we will be attending the International Cryptographic Module Conference 2023 or ICMC 2023 in Ottawa, Canada this week. ICMC 23 is building on a decade of cybersecurity thought leadership as the industry faces widespread changes and emerging threats in commercial cryptography.
More ...Changes to OMC Membership
The OpenSSL Management Committee (OMC) represents the official voice of the project and is ultimately responsible for all decisions regarding management and strategic direction of the project.
You may have already seen the recent blog post about Mark Cox leaving the OMC.
Following on from that we are delighted to announce that Anton Arapov, our engineering manager, has now joined the OMC.
You can check our website for the full list of members.
More ...Mark Cox moves to OpenSSL alumni
This is the end of an era for OpenSSL with the last of the original founders of the project passing on the torch to the current leadership of the project for the next phase of its evolution.
More ...OpenSSL Updates: A Few Steps Forward
At OpenSSL, we’re always learning and taking small steps, informed by both fresh ideas and the feedback we receive. Today, we’d like to share a couple of updates we hope will make things clearer and more collaborative for our community.
These updates are part of our effort to align more closely with, and live by, our Mission and Values.
More ...OpenSSL Finances
We recently published our mission statement and values which included that our governance should be transparent. We’ve not really talked much about how we’re financed and where the money goes, so let’s make a start on changing that.
A little background for clarity: The OpenSSL project has two companies, registered in the USA.https://openssl-corporation.org/support/ The first, OpenSSL Software Foundation, is a non-profit organisation that is used to hold the copyrights, trademarks, as well as things like the contributor license agreements (CLA). The second, OpenSSL Software Services, is our commercial entity that provides companies with paid support and other services, and pays our consultants to work on those services as well as development on OpenSSL. The OpenSSL project relies on funding to maintain and improve OpenSSL, and the goal of OpenSSL Software Services is to ensure long term sustainable funding to the project.
More ...OpenSSL is looking to contract a full-time Community Engagement Leader / Evangelist
UPDATE: Please note this position has been filled.
Job Description
We are seeking a passionate, tech-savvy individual to act as a Community Engagement Leader for the OpenSSL project. The ideal candidate will be responsible for fostering and enhancing connections between various communities around OpenSSL, facilitating fruitful discussions, spreading awareness about the project, and driving engagement and contributions. An essential aspect of this role is alignment with our core values and mission, as we expect these principles to be reflected in your day-to-day professional activities. Beyond community engagement, this role also involves collecting and contributing valuable insights to the project’s roadmap, making it an integral part of the project’s continuous growth and improvement.
This is a remote position with travel required, approximately up to 15% of working time. Given the global nature of the project, we require flexibility in accommodating various time zones outside of conventional business hours. We are seeking candidates located specifically within the Europe and North America.
To apply please send your resume to jobs@openssl.org by 17th August 2023.
Applications will be reviewed on a rolling basis. Only candidates selected for interviews will be contacted.
More ...Who writes OpenSSL?
For a meeting last week I wanted to show how much of OpenSSL is being written by people paid to do so by their employers, and how much was from individuals in their own time. And it turns out most of OpenSSL is written by people paid to do so. This is crucial to understanding the critical role that corporations provide to Open Source projects such as OpenSSL.
More ...OpenSSL adopts Mission & Values Statement
After extensive feedback from our communities, OpenSSL is pleased to announce that we have formally adopted the Mission and Values Statement, and will now be aligning our activities to support these.
You can view our new Mission and Values Statment here.
We would like to extend our sincere thanks to all those who provided feedback to us. We have reviewed all the comments and responses, which showed that a clear majority (around 70%) agreed on OpenSSL adopting the Mission and Values Statement. It was really beneficial to hear from our various communities and we will continue to seek out your feedback in the future.
More ...OpenSSL extends feedback on draft mission & values statement
OpenSSL would like to thank everyone who has provided feedback on our draft mission & values statement. The response has been great, and the feedback is really important to us. We are working through those responses.
We’d like to get even more feedback so we are extending the response period until 19th May 2023. If you haven’t already provided feedback to us, please do so by:
- Filling in this feedback form, or
- Emailing your feedback to feedback@openssl.org
As a small incentive we will be randomly selecting 10 responders out of everyone who has provided feedback and the lucky ones will receive an OpenSSL T-shirt. (Yes this includes those who have already responded to us).
More ...Meet Anton Arapov: The Latest Addition to the OpenSSL Team
We are thrilled to announce that Anton Arapov has joined the OpenSSL team! Anton brings a wealth of experience to the project, having previously worked on the Linux kernel, telecom core services, and cloud infrastructure management software as an engineering and project manager. He’s deeply committed to open-source software and will undoubtedly propel the OpenSSL project forward with his expertise and knowledge.
More ...OpenSSL seeks feedback on draft mission & values statement
Following the successful OpenSSL 2023 face-to-face conference, OpenSSL has produced a draft mission & values statement. Once finalised, we intend to realign all activities of the project to ensure they reflect our agreed mission and values. Before doing so however, we would like to obtain feedback on this statement from the public, to ensure it represents all of our communities. By offering us your feedback, you will help us to ensure the OpenSSL project is run in a way that reflects the values of all of our users.
More ...OpenSSL Face-to-Face Conference 2023
![[Photo of OpenSSL F2F 2023 attendees]]( /images/blog/f2f-2023.jpg)
In February 2023, the OpenSSL project held a face-to-face meeting in Queensland, Australia, which was attended by most of the project’s full-time contractors and OMC members. Amongst other subjects, the conference aimed to identify how OpenSSL can improve its governance and better execute on its mission.
More ...OpenSSL is looking for a full time Administrator and Manager
The OpenSSL Management Committee are looking to hire a full time Administrator and Manager. Details of the role follow.
To apply please send your cover letter and resume to jobs@openssl.org by 20th September 2020.
More ...Security Policy Update on prenotifications
We’re planning to extend who we prenotify of any future High and Critical security issues.
More ...QUIC and OpenSSL
QUIC is a new protocol which the IETF talks about as A UDP-Based Multiplexed and Secure Transport, and has attracted a lot of attention lately. The OpenSSL Management Committee (OMC) have followed the development with interest, and we feel that we owe it to the community to say where we stand on this, and on the inclusion of support for this protocol in our libraries.
More ...Update on 3.0 Development, FIPS and 1.0.2 EOL
We have previously talked about our plans for OpenSSL 3.0 and FIPS support here. This blog post will give an update about what has been happening since then.
More ...Face to Face: Committer's Day
At the Face to Face meeting held on the occasion of the ICMC19 Conference in Vancouver, a novelty was introduced: For the last day of the meeting all committers were invited to participate, either personally or remotely via video conference.
More ...OpenSSL 3.0 and FIPS update
As mentioned in a previous blog post, OpenSSL team members met with various representatives of the FIPS sponsor organisations back in September last year to discuss design and planning for the new FIPS module development project.
Since then there has been much design work taking place and we are now able to publish the draft design documentation. You can read about how we see the longer term architecture of OpenSSL changing in the future here and you can read about our specific plans for OpenSSL 3.0 (our next release which will include a FIPS validated module) here.
More ...Celebrating 20 years of OpenSSL
20 years ago, on the 23rd December 1998, the first version of OpenSSL was released. OpenSSL was not the original name planned for the project but it was changed over just a few hours before the site went live. Let’s take a look at some of the early history of OpenSSL as some of the background has not been documented before.
More ...The Holy Hand Grenade of Antioch
The OpenSSL Management Committee has been looking at the versioning scheme that is currently in use. Over the years we’ve received plenty of feedback about the “uniqueness” of this scheme, and it does cause some confusion for some users. We would like to adopt a more typical version numbering approach.
The current versioning scheme has this format:
MAJOR.MINOR.FIX[PATCH]
The new scheme will have this format:
MAJOR.MINOR.PATCH
In practical terms our “letter” patch releases become patch numbers and “fix” is dropped from the concept. In future, API/ABI compatibility will only be guaranteed for the same MAJOR version number. Previously we guaranteed API/ABI compatibility across the same MAJOR.MINOR combination. This more closely aligns with the expectations of users who are familiar with semantic versioning. We are not at this stage directly adopting semantic versioning because it would mean changing our current LTS policies and practices.
More ...FIPS 140-2: Forward progress
The OpenSSL Management Committee (OMC) on behalf of the OpenSSL Project would like to formally express its thanks to the following organisations for agreeing to sponsor the next FIPS validation effort: Akamai Technologies, Blue Cedar, NetApp, Oracle, VMware.
Four weeks ago, the OpenSSL team gathered with many of the organisations sponsoring the next FIPS module for a face-to-face meeting in Brisbane, Australia.
We got a great deal accomplished during that week. Having most of the fips-sponsor organisations in the same location helps ensure that we are all on the same page for the decisions we need to make going forward.
More ...OpenSSL 1.1.1 is released
After two years of work we are excited to be releasing our latest version today - OpenSSL 1.1.1. This is also our new Long Term Support (LTS) version and so we are committing to support it for at least five years.
OpenSSL 1.1.1 has been a huge team effort with nearly 5000 commits having been made from over 200 individual contributors since the release of OpenSSL 1.1.0. These statistics just illustrate the amazing vitality and diversity of the OpenSSL community. The contributions didn’t just come in the form of commits though. There has been a great deal of interest in this new version so thanks needs to be extended to the large number of users who have downloaded the beta releases to test them out and report bugs.
More ...New OMC member and new Committers
We first announced last year the OpenSSL Management Committee and separate Committers groups aimed at enabling greater involvement from the community.
We have now added a new OMC member and two new committers.
More ...New LTS Release
Back around the end of 2014 we posted our release strategy. This was the first time we defined support timelines for our releases, and added the concept of an LTS (long-term support) release. At our OMC meeting earlier this month, we picked our next LTS release. This post walks through that announcement, and tries to explain all the implications of it.
More ...Seeking Last Group of Contributors
The following is a press release that we just put out about how finishing off our relicensing effort. For the impatient, please see https://license.openssl.org/trying-to-find to help us find the last people; we want to change the license with our next release, which is currently in Alpha, and tentatively set for May.
For background, you can see all posts in the license tag.
One copy of the press release is at https://www.prnewswire.com/news-releases/openssl-seeking-last-group-of-contributors-300607162.html.
More ...Another Face to Face: Email changes and crypto policy
The OpenSSL OMC met last month for a two-day face-to-face meeting in London, and like previous F2F meetings, most of the team was present and we addressed a great many issues. This blog posts talks about some of them, and most of the others will get their own blog posts, or notices, later. Red Hat graciously hosted us for the two days, and both Red Hat and Cryptsoft covered the costs of their employees who attended.
One of the overall threads of the meeting was about increasing the transparency of the project. By default, everything should be done in public. We decided to try some major changes to email and such.
More ...OpenSSL wins the Levchin prize
Today I have had great pleasure in attending the Real World Crypto 2018 conference in Zürich in order to receive the Levchin prize on behalf of the OpenSSL team.
The Levchin prize for Real World Cryptography recognises up to two groups or individuals each year who have made significant advances in the practice of cryptography and its use in real-world systems. This year one of the two recipients is the OpenSSL team. The other recipient is Hugo Krawczyk.
More ...More China press coverage
Press Coverage
There have been more articles written based on the interviews with Paul Yang from BaishanCloud, Tim Hudson, and Steve Marquess from the OpenSSL team.
These join the articles noted in the previous blog entry.
Seven days and four cities in China
We had been invited to spend time with the open source community in China by one of the developers - Paul Yang - who participates in the OpenSSL project. A number of the team members had communicated via email over the last year and when the suggestion was made there were enough of us willing and interested to visit China for a “tour” to make sense. So the tour was agreed as a good thing and that started the journey that lead to spending a week in China (last week as I write this on the plane on the way back to Australia).
More ...OpenSSL goes to China
Over the past few years we’ve come to the realisation that there is a surprising (to us) amount of interest in OpenSSL in China. That shouldn’t have been a surprise as China is a huge technologically advanced country, but now we know better thanks to correspondence with many new Chinese contacts and the receipt of significant support from multiple Chinese donors (most notably from Smartisan.
We have accepted an invitation from BaishanCloud to visit China in person and meet with interested OpenSSL users and stakeholders in September. We’d like to thank BaishanCloud for hosting us and Paul Yang and his colleagues there for the substantial amount of work that went into arranging this trip.
More ...FIPS 140-2: Thanks and Farewell to SafeLogic
We’ve had a change in the stakeholder aspect of this new FIPS 140 validation effort. The original sponsor, SafeLogic, with whom we jump-started this effort a year ago and who has worked with us since then, is taking a well-deserved bow due to a change in circumstances. Supporting this effort has been quite a strain for a relatively small company, but SafeLogic has left us in a fairly good position. Without SafeLogic we wouldn’t have made it this far, and while I don’t anticipate any future SafeLogic involvement with this effort from this point on, I remain enormously grateful to SafeLogic and CEO Ray Potter for taking on such a bold and ambitious venture.
More ...FIPS 140-2: And so it begins
It’s been almost a year since plans for a new FIPS 140 validation were first announced. Several factors have led to this long delay. For one, we chose to focus our limited manpower resources on higher priority objectives such as the TLS 1.3 implementation. SafeLogic has also experienced difficulties in obtaining the funding for their intended sponsorship; potential sponsors can contact them directly.
With TLS 1.3 now done (pending only a final TLS 1.3 specification) we’re now in a position to turn our attention to the new FIPS module, and just in the nick of time Oracle has pledged enough funding to get us off to a good start. With financial support from the Linux Foundation Core Infrastructure Initiative temporarily interrupted, leaving a team member with no income, that funding eases the pressure to seek new long term employment.
More ...New Committers
We announced back in October that we would be changing from a single OpenSSL Project Team to having an OpenSSL management committee and a set of committers which we planned to expand to enable the greater involvement from the community.
Now that we have in place committer guidelines, we have invited the first set of external (non-OMC) community members to become committers and they have each accepted the invitation.
More ...Licensing Update
The following is a press release that we just released, with the cooperation and financial support of the Core Infrastructure Initiative and the Linux Foundation.
In the next few days we’ll start sending out email to all contributors asking them to approve the change. In the meantime, you can visit the licensing website and search for your name and request the email. If you have changed email addresses, or want to raise other issues about the license change, please email license@openssl.org. You can also post general issues to openssl-users@openssl.org.
We are grateful to all the contributors who have contributed to OpenSSL and look forward to their help and support in this effort.
The official press release can be found at the CII website. The rest of this post is a copy:
More ...Project Bylaws
Last October, the OpenSSL Project team had a face to face meeting. We talked about many topics but one of them was that, in recent years, we have seen much more involvement from the community and that we would like to encourage that further. For example, there are a number of people in the community who we know and trust. We would like those people to get involved more and make it easier for them to contribute. We decided to introduce the concept of a “committer” (borrowed from the Apache concept): someone who has the ability to commit code to our source code repository but without necessarily having to become a full team member. This might be seen as a stepping-stone for someone who aspires to full team membership, or simply as an easier way of contributing for those that don’t. Those people could help with our review process (i.e., their reviews would count towards approval) - which might help us keep on top of the github issues and pull request queues.
More ...OCAP audit of OpenSSL
The audit took place during 2015 in two phases while the OpenSSL project was working on the development of the (now released) 1.1.0 version. We chose to audit the “master” branch of the code as it stood at the time. OpenSSL 1.1.0 has made some extensive internal changes, most notably in libssl with the new state machine code, as well as the new packet parsing code. We wanted the audit team to review that code to give us confidence that what we were delivering was sound.
More ...Face to Face: Roadmap and platform updates
This is another in the series of posts about decisions we made at our face-to-face meeting a couple of weeks ago.
We updated the project roadmap.
I think the most important news here, is that our next release will include TLS 1.3. Our current plan is that this will be 1.1.1, which means that it is API-compatible with the current 1.1.0 release. This is really only possible because of the work we did on making most of the structure internals opaque. Also, since we are doing all of our work in public on our GitHub repository, we hope that the entire community will be able to “follow along at home” and help us improve the code. There will be more, much more, to say about this later.
More ...FIPS 140-2: Once more unto the breach
The last post on this topic sounded a skeptical note on the prospects for a new FIPS 140 validated module for OpenSSL 1.1 and beyond. That post noted a rather improbable set of prerequisites for a new validation attempt; ones I thought only a governmental sponsor could meet (as was the case for the five previous open source based validations).
Multiple commercial vendors have offered to fund (very generously in some cases) a new validation effort under terms that would guarantee them a proprietary validation, while not guaranteeing an open source based validation. At one point we actually came close to closing a deal that would have funded an open source based validation attempt in exchange for a limited period of exclusivity; a reasonable trade-off in my opinion. But, I eventually concluded that was too risky given an uncertain reception by the FIPS validation bureaucracy, and we decided to wait for a “white knight” sponsor that might never materialize.
More ...New severity level, "Critical"
We’ve just added a new severity level called “critical severity” to our security policy. When we first introduced the policy, over a year ago, we just had three levels, “Low”, “Moderate”, and “High”. So why did we add “Critical” and why are we not using someone else’s standard definitions?
After introducing the new policy we started giving everyone a headsup when we were due to release OpenSSL updates that included security fixes. The headsup doesn’t contain any details of the issues being fixed apart from the maximum severity level and a date a few days in the future.
More ...FIPS 140-2: It's not dead, it's resting
Some of you may have noticed that the upcoming 1.1 release doesn’t include any FIPS support. That omission is not by choice; it was forced on us by circumstances and will hopefully not be permanent.
The v2.0 OpenSSL FIPS module is compatible with the 1.0.x releases, in particular the 1.0.2 “LTS” release that will be supported through 2019. It has proven very popular, used both directly by hundreds of software vendors and indirectly as a model for copycat “private label” validations.
More ...OpenSSL Security: A Year in Review
Over the last 10 years, OpenSSL has published advisories on over 100 vulnerabilities. Many more were likely silently fixed in the early days, but in the past year our goal has been to establish a clear public record.
In September 2014, the team adopted a security policy that defines how we handle vulnerability reports. One year later, I’m very happy to conclude that our policy is enforced, and working well.
Our policy divides vulnerabilities into three categories, and defines actions for each category: we use the severity ranking to balance the need to get the fix out fast with the burden release upgrades put on our consumers.
More ...License Agreements and changes are coming
The OpenSSL license is rather unique and idiosyncratic. It reflects views from when its predecessor, SSLeay, started twenty years ago. As a further complication, the original authors were hired by RSA in 1998, and the code forked into two versions: OpenSSL and RSA BSAFE SSL-C. (See Wikipedia for discussion.) I don’t want get into any specific details, and I certainly don’t know them all.
Things have evolved since then, and open source is an important part of the landscape – the Internet could not exist without it. There are good reasons why Microsoft is a founding member of the Core Infrastructure Initiative (CII).
Our plan is to update the license to the Apache License version 2.0. We are in consultation with various corporate partners, the CII, and the legal experts at the Software Freedom Law Center. In other words, we have a great deal of expertise and interest at our fingertips.
More ...Logjam, FREAK and upcoming changes in OpenSSL
Today, news broke of Logjam, an attack on TLS connections using Diffie-Hellman ciphersuites. To protect OpenSSL-based clients, we’re increasing the minimum accepted DH key size to 768 bits immediately in the next release, and to 1024 bits soon after. We have also made several other changes to strengthen our cryptographic defaults and have updated our tools and documentation to help servers configure Diffie-Hellman ciphersuites securely - see below for details.
More ...




